D E Shaw Interview Questions

Table Of Contents
- Work Culture at D.E. Shaw
- Interview Process: What to Expect?
- D E Technical Interview Questions
- D.E. Shaw Interview Questions: Must-Prepare Topics
- Frequently Asked Questions ( FAQ’S )
- Tips to Crack the D.E. Shaw Interview
The IT industry has been booming for years, and one company that has consistently grown in this sector is D.E. Shaw. Founded by David E. Shaw in 1988, it is a global investment and technology development firm known for its innovative approach, dynamic leadership, and talented workforce. With offices in North America, Europe, and Asia, D.E. Shaw continues to set industry benchmarks in technology and finance.
Work Culture at D.E. Shaw
D.E. Shaw is recognized for its collaborative and inclusive work environment. Employees appreciate the strong work-life balance, open discussions, and continuous learning opportunities. The company fosters an innovative mindset where employees are encouraged to develop and implement new ideas.
Some key highlights of D.E. Shaw’s work culture include:
✔ Team Collaboration – Open discussions and teamwork drive successful projects.
✔ Continuous Learning – Employees experience new challenges every day, keeping them engaged.
✔ Career Growth – The company supports skill enhancement and professional development.
✔ Supportive Environment – Leaders and colleagues provide guidance and assistance.
For many employees, D.E. Shaw is more than just a workplace; it is a platform for growth and innovation. Whether you’re an intern or a seasoned professional, the company ensures that you stay motivated, challenged, and inspired.
Kickstart your Salesforce career with our Salesforce training in Hyderabad, featuring hands-on experience and real-world projects to build job-ready skills. Join us for a free demo session today!
D.E. Shaw Interview Process: What to Expect?
Before starting your journey with D.E. Shaw, it is essential to understand its interview process, core values, and hiring principles. The company looks for candidates with a strong analytical mindset, technical expertise, and problem-solving skills.
To help you navigate the selection process effectively, here’s a step-by-step breakdown of what to expect when interviewing at D.E. Shaw.
1. Application & Resume Shortlisting
The first step in the hiring process is submitting an online application through D.E. Shaw’s career portal or campus recruitment channels. The recruitment team carefully reviews resumes to shortlist candidates based on:
✔ Academic background – Strong GPA, coursework in relevant fields.
✔ Technical expertise – Programming skills, software development experience.
✔ Projects & internships – Hands-on experience in real-world applications.
✔ Problem-solving ability – Competitive programming, research papers, or hackathon experience.
💡 Tip: Tailor your resume to highlight skills and experiences relevant to the role you’re applying for.
2. Online Assessment (OA) – Coding & Aptitude Test
If shortlisted, you will receive an invitation to D.E. Shaw’s Online Assessment (OA). The test duration varies from 60 to 120 minutes, depending on the role.
Online Assessment Format:
🔹 Coding Round – Focuses on data structures, algorithms, and problem-solving.
🔹 Aptitude & Logical Reasoning – Tests mathematical and analytical thinking.
🔹 Technical MCQs – Covers OS, DBMS, OOPs, Computer Networks (role-specific).
🔹 Puzzle-solving questions – Measures logical thinking and creativity.
💡 Tip: Practice coding on Leetcode, CodeChef, and HackerRank to improve problem-solving speed.
See also: Siemens Interview Questions
3. Technical Interviews – Core Skills Assessment
After clearing the online assessment, candidates move on to multiple rounds of technical interviews conducted by senior developers, engineers, or research professionals at D.E. Shaw.
Each technical round lasts 45 to 60 minutes and can be virtual or in-person.
Key Focus Areas in Technical Interviews:
✅ Data Structures & Algorithms (DSA) – Arrays, Linked Lists, Trees, Graphs, Dynamic Programming.
✅ System Design – Scalability, Microservices, Caching strategies (for experienced roles).
✅ Database Management (DBMS) – SQL queries, Normalization, Transactions.
✅ Object-Oriented Programming (OOPs) – Encapsulation, Polymorphism, Design Patterns.
✅ Operating Systems & Networks – Threads, Memory management, Protocols.
✅ Competitive Coding Problems – Time complexity optimization, edge case handling.
💡 Tip: Be prepared to write and explain your code, optimize solutions, and discuss real-world applications of concepts.
4. Hiring Manager/Team Fit Round
Once you clear the technical interviews, you will have a discussion with a hiring manager or senior team members.
Key Aspects Covered:
🔹 Role Expectations – Responsibilities and challenges in the job.
🔹 Past Projects – Detailed discussion on projects mentioned in your resume.
🔹 Problem-Solving Approach – How you analyze and approach technical problems.
🔹 Team Collaboration – Experience working in teams, handling conflicts, and leading initiatives.
💡 Tip: Show your passion for technology and problem-solving skills with real-life examples.
5. HR & Behavioral Interview
The final stage is the HR round, where recruiters assess your cultural fit, career aspirations, and interpersonal skills.
Common HR Questions at D.E. Shaw:
✔ Tell me about yourself.
✔ Why do you want to work at D.E. Shaw?
✔ Describe a challenging project you worked on.
✔ How do you handle pressure and tight deadlines?
✔ Where do you see yourself in five years?
💡 Tip: Use the STAR Method (Situation, Task, Action, Result) to structure your answers concisely.
See also: HCL Interview Questions
6. Final Selection & Offer Letter
After successfully completing all rounds, the recruitment team evaluates your performance and provides feedback within a week. If selected, you will receive an offer letter detailing your compensation, role expectations, and joining formalities.
Post-Selection Steps:
✔ Salary Negotiation (if needed)
✔ Background Verification
✔ Onboarding Process & Training Plan
💡 Tip: Once selected, connect with current employees on LinkedIn to understand work culture and growth opportunities at D.E. Shaw.
D E Technical Interview Questions
1. What is a MAC address and how many bits does it consist of?
A MAC (Media Access Control) address is a unique identifier assigned to a network interface card (NIC) for communication on a network. It is a hardware address that helps devices communicate over a local network, ensuring data reaches the correct recipient. Every MAC address is globally unique and is embedded in the hardware by the manufacturer. It is used in Ethernet, Wi-Fi, and other networking technologies for device identification and communication.
A MAC address consists of 48 bits (6 bytes) and is usually written in hexadecimal format such as 00:1A:2B:3C:4D:5E. The first 24 bits represent the Organizationally Unique Identifier (OUI) assigned to the manufacturer, while the last 24 bits are the device-specific identifier. MAC addresses operate at the data link layer (Layer 2) of the OSI model and are essential for network communication, especially in LANs and wireless networks.
2. State some design issues of a computer network.
Designing a computer network involves several challenges that impact its performance, security, and scalability. One of the major design issues is network congestion, where excessive data traffic can slow down communication. Proper bandwidth management and load balancing are required to prevent this. Scalability is another concern, as networks must be designed to handle increasing devices and traffic without performance degradation.
Security threats also pose a significant design challenge. Networks are vulnerable to hacking, malware, and unauthorized access, so implementing firewalls, encryption, and authentication protocols is essential. Other design issues include fault tolerance, ensuring the network remains operational even if components fail, and interoperability, where devices and protocols from different vendors must work seamlessly together. A well-designed network should balance performance, security, and cost-effectiveness while ensuring ease of maintenance.
3. Explain the term checksum error correction.
Checksum error correction is a method used in data transmission to ensure that information is received without errors. When data is sent over a network, it can be corrupted due to noise, signal interference, or hardware failures. A checksum is a small-sized data value calculated from the original data and sent along with it. The receiving end recalculates the checksum and compares it with the received checksum to detect errors. If they match, the data is correct; otherwise, an error has occurred.
There are different types of checksum methods, such as parity checks, cyclic redundancy check (CRC), and Fletcher’s checksum. These techniques enhance error detection but do not always guarantee error correction. In case of an error, the system may request retransmission (Automatic Repeat Request – ARQ) or apply forward error correction (FEC) techniques. By implementing checksum error correction, we can increase data reliability in communication systems, particularly in network protocols, file transfers, and disk storage.
See also: PayTM Interview Questions
4. What do you mean by the semantic gap?
The semantic gap refers to the difference between high-level human understanding and low-level computer representations. In computing and software engineering, humans think in abstract, meaningful concepts, whereas computers process binary data and instructions. Bridging this gap is essential for efficient human-computer interaction, software design, and AI development.
For example, in image processing, humans recognize objects like “car” or “tree,” but computers see them as pixel values and numerical patterns. Similarly, in programming languages, developers write high-level code, which compilers convert into low-level machine instructions. The semantic gap is addressed through abstraction layers, artificial intelligence, and machine learning techniques, making systems more user-friendly.
Some key areas where the semantic gap is evident include:
- Natural Language Processing (NLP): Converting human speech into machine-understandable commands.
- Database Queries: Translating user-friendly queries into optimized SQL commands.
- Image and Video Recognition: AI-based interpretation of images for object detection.
- Software Development: Compilers and interpreters bridging human logic and machine code.
Reducing the semantic gap is crucial for advancing AI, improving user experience, and optimizing automation in various fields.
5. What does cycle stealing mean?
Cycle stealing is a technique used in computer architecture and direct memory access (DMA) operations, where a device temporarily halts the CPU to access memory. Instead of waiting for the CPU to finish its operations, peripheral devices like disk controllers and network interfaces “steal” CPU cycles to perform memory transfers. This helps in efficient multitasking but may slow down the CPU’s main processing tasks.
For example, in DMA-based data transfer, a device moves data from memory without CPU intervention. The CPU is temporarily paused while the DMA controller reads or writes data, reducing CPU overhead. However, excessive cycle stealing can lead to performance degradation, making it essential to balance CPU and device priorities.
Some common areas where cycle stealing is used:
- DMA Transfers: Moving data between memory and peripherals.
- I/O Operations: Fetching data from storage or network devices.
- Interrupt Handling: Devices interrupting the CPU for urgent processing.
While cycle stealing improves overall system efficiency, improper use can lead to CPU slowdowns and bottlenecks. Balancing it effectively ensures smooth multitasking and better performance.
6. When is a switch considered congested?
A switch is considered congested when it receives more traffic than it can handle, leading to packet drops, increased latency, and performance degradation. Network switches process and forward packets between devices, but when the incoming data rate exceeds the switch’s processing capacity, congestion occurs. This typically happens in high-traffic environments where multiple devices send large amounts of data simultaneously, overloading the switch buffers.
Congestion can also occur due to poor network design, lack of bandwidth, or inefficient load balancing. When a switch becomes congested, it may start dropping packets (packet loss), which negatively affects network performance. To handle congestion, we can use techniques such as Quality of Service (QoS), VLAN segmentation, and upgrading to higher-capacity switches. Proper network monitoring and traffic management help in reducing congestion and ensuring smooth data transmission.
7. What is a semaphore and what are its uses?
A semaphore is a synchronization mechanism used in multithreading and process control to manage access to shared resources. It helps in preventing race conditions and deadlocks by restricting the number of processes or threads that can access a resource at a given time. Semaphores can be binary (mutex) or counting, where a binary semaphore allows only one process at a time, and a counting semaphore allows multiple processes up to a predefined limit.
Semaphores are widely used in operating systems, databases, and concurrent programming. For example, in a printer queue, a semaphore ensures that only one job accesses the printer at a time. In database management systems (DBMS), semaphores prevent multiple transactions from modifying the same record simultaneously. By implementing semaphores, I can ensure thread-safe operations, controlled resource allocation, and improved process synchronization in concurrent environments.
See also: Avasoft Interview Questions
8. Explain the terms demand-paging and pre-paging.
Demand-paging is a memory management technique in which pages are loaded into RAM only when needed, reducing initial memory usage. When a program starts executing, only essential pages are loaded, and any additional pages required generate a page fault. The operating system then retrieves the missing page from disk and loads it into memory. This approach is efficient for minimizing memory waste but may cause performance delays due to frequent page faults.
Pre-paging, on the other hand, is the process of loading additional pages into memory before they are explicitly requested. The system predicts which pages will be needed soon and loads them in advance to reduce page faults. While pre-paging can improve performance by anticipating future needs, it may also lead to wasted memory if the preloaded pages are never used. Both techniques aim to optimize memory usage and improve execution speed, and their effectiveness depends on the system workload and access patterns.
9. What is the use of the volatile keyword in Java?
The volatile keyword in Java is used to ensure that a variable’s value is always read from main memory rather than a thread’s local cache. This is crucial in multithreaded programming, where different threads may access and modify shared variables. Without volatile, threads may work with outdated values, leading to unpredictable behavior and race conditions.
For example, in a multithreaded application, if one thread updates a shared variable and another thread reads it, volatile ensures the latest value is always read. Here’s an example of how volatile is used:
class SharedResource {
volatile boolean flag = false;
void updateFlag() {
flag = true; // Immediately visible to all threads
}
}By declaring flag as volatile, I ensure that changes made by one thread are instantly visible to all other threads. However, volatile does not provide atomicity, so for complex operations like incrementing a counter, I use synchronized blocks or Atomic variables instead.
10. How can you implement a queue using a stack?
A queue follows the FIFO (First In, First Out) principle, whereas a stack operates on LIFO (Last In, First Out). To implement a queue using two stacks, I can use either:
- Enqueue operation costly: Move all elements from Stack 1 to Stack 2, push the new element, then move everything back.
- Dequeue operation costly: Push elements into Stack 1 normally and only move them to Stack 2 when needed for removal.
Here’s a simple Java implementation using two stacks:
import java.util.Stack;
class QueueUsingStack {
Stack<Integer> stack1 = new Stack<>();
Stack<Integer> stack2 = new Stack<>();
void enqueue(int value) {
stack1.push(value);
}
int dequeue() {
if (stack2.isEmpty()) {
while (!stack1.isEmpty()) {
stack2.push(stack1.pop());
}
}
return stack2.isEmpty() ? -1 : stack2.pop();
}
}In this approach, I use two stacks to manage the queue’s order. The enqueue() function pushes elements into stack1, and the dequeue() function moves elements to stack2 only when necessary. This method ensures a functional queue behavior using stacks, though it may involve additional overhead in moving elements between stacks.
11. Can you tell the Time Complexity for Searching an Element in a HashMap
In a HashMap, the time complexity for searching an element is O(1) on average. This is because a HashMap stores key-value pairs and uses a hash function to compute the index of the bucket where the value is stored.
Explanation:
- When you perform a search operation (like
get(key)), the hash function is used to determine the bucket. Then, the key-value pair is searched in that bucket. - In the worst-case scenario (if many keys hash to the same bucket), the time complexity could degrade to O(n), where n is the number of elements in the HashMap. However, this is rare and usually mitigated by a good hash function.
Example:
import java.util.HashMap;
public class HashMapSearch {
public static void main(String[] args) {
HashMap<String, Integer> map = new HashMap<>();
map.put("A", 1);
map.put("B", 2);
// Searching for the element 'B'
int value = map.get("B"); // O(1) on average
System.out.println(value); // Output: 2
}
}Output:
2The code uses map.get("B") to search for the value of key "B". It prints the result, which is 2.
See also: Linkedin Interview Questions
12. How can you search for an element in a rotated sorted array?
A rotated sorted array is an array that was originally sorted but later rotated at some pivot. To efficiently search for an element in such an array, I use modified binary search with O(log n) complexity. The key observation is that at least one half of the array remains sorted after rotation.
Approach:
- Identify the midpoint and check if it’s the target element.
- Determine if the left or right half is sorted.
- If the left half is sorted, check if the target lies within its range; otherwise, search in the right half.
- Repeat this process until the element is found or the search space is exhausted.
Example Code:
public class RotatedArraySearch {
public static int search(int[] arr, int target) {
int left = 0, right = arr.length - 1;
while (left <= right) {
int mid = left + (right - left) / 2;
if (arr[mid] == target) return mid;
if (arr[left] <= arr[mid]) { // Left half is sorted
if (target >= arr[left] && target < arr[mid])
right = mid - 1;
else
left = mid + 1;
} else { // Right half is sorted
if (target > arr[mid] && target <= arr[right])
left = mid + 1;
else
right = mid - 1;
}
}
return -1;
}
public static void main(String[] args) {
int[] arr = {4, 5, 6, 7, 0, 1, 2};
System.out.println(search(arr, 6)); // Output: 2
}
}This method ensures efficient O(log n) search even in a rotated array.
13. Determine if there is any subarray present whose sum is 0.
To check for a subarray with sum 0, I can use a HashSet to track cumulative sums. If the same sum appears more than once, it means that the intermediate subarray between these occurrences has a sum of zero.
Approach:
- Initialize
sum = 0and a HashSet to store seen sums. - Traverse the array and keep adding elements to
sum. - If
sum == 0or already exists in the HashSet, a subarray with zero sum exists.
Example Code:
import java.util.HashSet;
public class ZeroSumSubarray {
public static boolean hasZeroSumSubarray(int[] nums) {
HashSet<Integer> prefixSums = new HashSet<>();
int sum = 0;
for (int num : nums) {
sum += num;
if (sum == 0 || prefixSums.contains(sum)) {
return true;
}
prefixSums.add(sum);
}
return false;
}
public static void main(String[] args) {
int[] nums = {4, -3, 2, 1};
System.out.println(hasZeroSumSubarray(nums)); // Output: true
}
}Output
trueThe code detects that there is a subarray ({4, -3, -1}) that sums to 0, and it prints true.
14. Find the peak element in a given array.
A peak element is an element that is greater than its neighbors. If the array is sorted, the last element is the peak. However, for an unsorted array, I use binary search for O(log n) time complexity.
Approach:
- Identify the mid element.
- If
midis greater than both its neighbors, return it as the peak. - If the left neighbor is greater, move left; otherwise, move right.
Example Code:
public class PeakElement {
public static int findPeakElement(int[] nums) {
int left = 0, right = nums.length - 1;
while (left < right) {
int mid = left + (right - left) / 2;
if (nums[mid] < nums[mid + 1]) {
left = mid + 1; // move to the right half
} else {
right = mid; // move to the left half
}
}
return left; // peak element index
}
public static void main(String[] args) {
int[] nums = {1, 2, 3, 1};
System.out.println(findPeakElement(nums)); // Output: 2
}
}Output
2The peak element in the array {1, 2, 3, 1} is 3 at index 2, so it prints 2.
15. Sort an array relatively.
Relative sorting means sorting one array based on another array’s order. A common example is sorting an array while maintaining the relative order of another array’s elements.
Approach:
- Store the frequency of elements from the main array.
- Place elements in the sorted order according to a given order array.
- Append remaining elements in ascending order.
Example Code:
import java.util.*;
public class RelativeSorting {
public static int[] relativeSortArray(int[] arr1, int[] arr2) {
Map<Integer, Integer> freqMap = new HashMap<>();
for (int num : arr1)
freqMap.put(num, freqMap.getOrDefault(num, 0) + 1);
int index = 0;
for (int num : arr2) {
while (freqMap.getOrDefault(num, 0) > 0) {
arr1[index++] = num;
freqMap.put(num, freqMap.get(num) - 1);
}
}
List<Integer> remaining = new ArrayList<>();
for (int num : freqMap.keySet()) {
while (freqMap.get(num) > 0) {
remaining.add(num);
freqMap.put(num, freqMap.get(num) - 1);
}
}
Collections.sort(remaining);
for (int num : remaining)
arr1[index++] = num;
return arr1;
}
public static void main(String[] args) {
int[] arr1 = {2, 3, 1, 3, 2, 4, 6, 7, 9, 2, 19};
int[] arr2 = {2, 1, 4, 3, 9, 6};
System.out.println(Arrays.toString(relativeSortArray(arr1, arr2)));
}
}This approach ensures relative ordering while maintaining efficiency.
16. Values in a Given Range of Elements
To find values in a given range within an array, we simply iterate through the array and check if each element is within the specified range.
Explanation:
- The problem can be solved by iterating over each element of the array.
- For each element, check if it is within the given range.
- If it is, store it in a result array or list.
Example:
import java.util.ArrayList;
import java.util.List;
public class RangeFilter {
public static List<Integer> valuesInRange(int[] arr, int min, int max) {
List<Integer> result = new ArrayList<>();
for (int num : arr) {
if (num >= min && num <= max) {
result.add(num);
}
}
return result;
}
public static void main(String[] args) {
int[] arr = {1, 5, 8, 12, 15, 3, 7};
int min = 5, max = 12;
System.out.println(valuesInRange(arr, min, max)); // Output: [5, 8, 12, 7]
}
}Output:
[5, 8, 12, 7]The code checks each number in the array {1, 5, 8, 12, 15, 3, 7} to see if it falls within the range [5, 12].
17. Calculate the Product of an Array Excluding the Present Value
To calculate the product of all elements in an array excluding the present value, we can use two methods: the prefix and suffix product arrays or the O(1) space solution using a single pass.
Explanation:
- Prefix Product: Store the product of all elements before a given element in the array.
- Suffix Product: Store the product of all elements after a given element.
- Multiply the prefix product and suffix product for each element to get the product excluding that element.
Example:
public class ProductOfArrayExceptSelf {
public static int[] productExceptSelf(int[] nums) {
int n = nums.length;
int[] result = new int[n];
int prefix = 1;
// Compute prefix products
for (int i = 0; i < n; i++) {
result[i] = prefix;
prefix *= nums[i];
}
int suffix = 1;
// Compute suffix products
for (int i = n - 1; i >= 0; i--) {
result[i] *= suffix;
suffix *= nums[i];
}
return result;
}
public static void main(String[] args) {
int[] nums = {1, 2, 3, 4};
int[] result = productExceptSelf(nums);
for (int num : result) {
System.out.print(num + " "); // Output: 24 12 8 6
}
}
}Output:
24 12 8 6The result array contains the product of all elements except the current one for each index.
18. Calculate the Number of Trailing 0s in 100!
The number of trailing zeroes in a factorial is determined by the number of factors of 10 in the number. Each factor of 10 comes from a pair of factors 2 and 5, but 2s are more frequent than 5s, so we count the number of times 5 is a factor.
Formula:
- The number of trailing zeros in n! is given by:
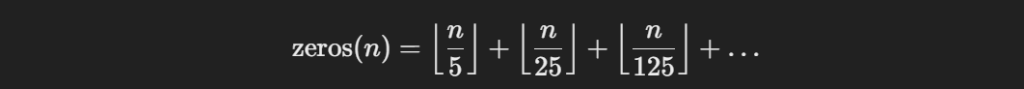
Explanation:
- For 100!, count how many multiples of 5, 25, 125, etc., are there up to 100.
Example:
public class TrailingZeroes {
public static int countTrailingZeroes(int n) {
int count = 0;
while (n >= 5) {
count += n / 5;
n /= 5;
}
return count;
}
public static void main(String[] args) {
int n = 100;
System.out.println(countTrailingZeroes(n)); // Output: 24
}
}Output:
24There are 24 trailing zeros in 100! as a result of the factors of 5.
19. Maximum Sum Subtree
The maximum sum subtree is a subtree of a binary tree where the sum of the node values is the highest. We can use post-order traversal to find the maximum sum subtree.
Explanation:
- Perform a post-order traversal (left-right-root) to calculate the sum of each subtree.
- Track the maximum sum encountered during the traversal.
Example:
class TreeNode {
int val;
TreeNode left, right;
TreeNode(int val) {
this.val = val;
left = right = null;
}
}
public class MaxSumSubtree {
static class Result {
int sum;
TreeNode node;
}
public static Result maxSumSubtree(TreeNode root) {
return maxSumSubtreeHelper(root).node;
}
private static Result maxSumSubtreeHelper(TreeNode root) {
if (root == null) {
return new Result();
}
Result left = maxSumSubtreeHelper(root.left);
Result right = maxSumSubtreeHelper(root.right);
int sum = root.val + left.sum + right.sum;
Result result = new Result();
result.sum = sum;
if (sum > left.sum && sum > right.sum) {
result.node = root;
} else if (left.sum > right.sum) {
result.node = left.node;
} else {
result.node = right.node;
}
return result;
}
public static void main(String[] args) {
TreeNode root = new TreeNode(1);
root.left = new TreeNode(2);
root.right = new TreeNode(3);
root.left.left = new TreeNode(4);
root.left.right = new TreeNode(5);
TreeNode maxSumNode = maxSumSubtree(root);
System.out.println(maxSumNode.val); // Output: 2
}
}Output:
2The subtree with the maximum sum is rooted at node 2, and the sum of this subtree is 11.
20. Test Cases for an ATM Machine
Test cases for an ATM machine should cover various scenarios including valid transactions, invalid inputs, balance checks, and error handling.
Common Test Cases:
1. Valid Withdrawal (Exact Balance)
Input: Withdraw $50 from an account with $50.
Expected Output: Withdrawal successful, balance is $0.
2. Valid Withdrawal (Partial Balance)
Input: Withdraw $40 from an account with $100.
Expected Output: Withdrawal successful, balance is $60.
3. Invalid Withdrawal (Insufficient Funds)
Input: Withdraw $200 from an account with $100.
Expected Output: Error message: “Insufficient funds.”
4. Valid Deposit
Input: Deposit $100 into an account with $50.
Expected Output: Deposit successful, new balance is $150.
5. Invalid Deposit (Exceeds Limit)
Input: Deposit $2000 into an account with a maximum deposit limit of $1500.
Expected Output: Error message: “Deposit limit exceeded.”
6. Account Balance Inquiry
Input: Check balance on an account with $200.
Expected Output: Balance: $200.
7. Invalid PIN Entry (Multiple Attempts)
Input: Enter an incorrect PIN 3 times consecutively.
Expected Output: Error message: “Account locked due to multiple incorrect PIN attempts.”
8. Transaction Receipt Printing
Input: Perform a withdrawal of $50.
Expected Output: Print a receipt showing transaction details and updated balance.
9. ATM Malfunction (Cash Out of Service)
Input: Attempt to withdraw money when the ATM is out of cash.
Expected Output: Error message: “ATM is out of cash, please try again later.”
10. Session Timeout
Input: Leave the ATM idle for 10 minutes.
Expected Output: Session expires, the user is logged out automatically.
D.E. Shaw Interview Questions: Must-Prepare Topics
To gain an edge over other candidates, it’s crucial to prepare for commonly asked D.E. Shaw interview questions. Below are some key areas you should focus on:
Technical Questions:
✔ Data Structures & Algorithms (Arrays, Linked Lists, Trees, Graphs)
✔ Database Management (SQL queries, Normalization, Indexing)
✔ Object-Oriented Programming (Encapsulation, Inheritance, Polymorphism)
✔ System Design (Scalability, Microservices, Load Balancing)
✔ Coding Challenges (Competitive programming concepts)
Behavioral & HR Questions:
✔ Why do you want to work at D.E. Shaw?
✔ Tell us about a challenging project you worked on.
✔ How do you handle tight deadlines and pressure?
✔ Describe a time when you faced a conflict in a team and how you resolved it.
✔ What are your long-term career goals?
Frequently Asked Questions ( FAQ’S )
1. What are some common technical questions asked in a D.E. Shaw interview?
In a D.E. Shaw interview, candidates can expect technical questions related to data structures, algorithms, system design, and problem-solving. They may be asked to write code on a whiteboard or solve algorithmic challenges in real-time. For example, questions like “How do you find the middle element of a linked list?” or “Design a system for URL shortening” are commonly asked. These questions test your analytical thinking and ability to write optimized code. A typical approach to solving such problems includes breaking the problem down into smaller subproblems, followed by choosing appropriate data structures and algorithms.
2. How should I prepare for the D.E. Shaw interview?
To prepare for the D.E. Shaw interview, it’s essential to practice coding problems on platforms like LeetCode, HackerRank, or CodeSignal, particularly focusing on problems involving arrays, strings, dynamic programming, and graph traversal. Brush up on your knowledge of core computer science concepts like time complexity analysis, sorting algorithms, and basic data structures (trees, heaps, queues). Additionally, be ready to discuss your past projects, particularly any work involving problem-solving and innovation. Interviewers may also ask behavioral questions, so preparing answers based on your experience and teamwork is key.
3. What is the interview process like at D.E. Shaw?
The interview process at D.E. Shaw generally consists of multiple rounds, starting with an online assessment or coding challenge. If successful, candidates are invited for technical interviews, which can include problem-solving, data structure-related questions, and system design questions. In some cases, there might be additional rounds that focus on behavioral interviews to assess cultural fit and interpersonal skills. Lastly, if you perform well in all rounds, you may be offered a final interview with the HR team to discuss compensation and other logistics.
4. How do you approach problem-solving questions in the D.E. Shaw interview?
When approaching problem-solving questions in the D.E. Shaw interview, always start by clearly understanding the problem statement. Then, break it down into smaller, manageable parts, and analyze the input-output behavior. Discuss the time and space complexity of your solution to show that you can optimize your approach. If applicable, consider edge cases and test your solution with sample inputs. Interviewers are not only looking for the right answer but also evaluating your thought process, clarity, and ability to articulate the solution.
5. Can you provide an example of a coding challenge asked at D.E. Shaw?
One common coding challenge at D.E. Shaw might be related to dynamic programming. For example, a question could be: “Given an array of integers, find the length of the longest increasing subsequence.” Here’s how you might approach it:
public class LongestIncreasingSubsequence {
public static int lengthOfLIS(int[] nums) {
if (nums.length == 0) return 0;
int[] dp = new int[nums.length];
Arrays.fill(dp, 1);
for (int i = 1; i < nums.length; i++) {
for (int j = 0; j < i; j++) {
if (nums[i] > nums[j]) {
dp[i] = Math.max(dp[i], dp[j] + 1);
}
}
}
return Arrays.stream(dp).max().getAsInt();
}
public static void main(String[] args) {
int[] nums = {10, 9, 2, 5, 3, 7, 101, 18};
System.out.println(lengthOfLIS(nums)); // Output: 4
}
}Explanation:
This dynamic programming solution calculates the length of the longest increasing subsequence.
We iterate over the array and update a dp array where dp[i] represents the length of the longest subsequence ending at index i.
The time complexity of this solution is O(n²).
Tips to Crack the D.E. Shaw Interview
To maximize your chances of getting hired at D.E. Shaw, follow these expert tips:
🔹 Master Core Concepts – Brush up on data structures, algorithms, and system design.
🔹 Practice Coding Regularly – Use platforms like Leetcode, CodeChef, and HackerRank.
🔹 Prepare Behavioral Questions – Structure your responses using the STAR (Situation, Task, Action, Result) method.
🔹 Revise Your Projects – Be ready to discuss your past internships, research, and technical contributions.
🔹 Stay Confident and Communicate Clearly – D.E. Shaw values candidates who can express their thoughts logically and confidently.
Summing Up
D.E. Shaw’s interview process challenges candidates with tough algorithmic and system design questions. Success hinges on strong problem-solving skills, technical knowledge, and a sharp ability to optimize solutions. Prepare thoroughly, as the process evaluates both your technical expertise and cultural fit.
Become a Salesforce Expert with Advanced Training in Hyderabad
Led by expert instructors, our Salesforce training includes personalized mentorship, interview coaching, and certification exam preparation to help you stand out in the job market. With hands-on projects, comprehensive study materials, and continuous guidance, you’ll build the confidence and expertise needed to earn top certifications and demonstrate practical skills that employers value.
Gain in-depth Salesforce training in Hyderabad, designed to provide a hands-on, immersive learning experience. This program covers Salesforce Admin, Developer, and AI domains, blending theoretical knowledge with real-world applications. Through industry-relevant projects and assignments, you’ll learn to tackle complex business challenges using Salesforce solutions while enhancing your problem-solving skills.
Start your Salesforce career today—register for a FREE demo session and unlock new career opportunities!

